
iExec is a decentralized infrastructure for cloud computing resources, with a complete solution to run privacy-preserving executions of any application. Developers and enterprises can use the iExec tools to monetize data, and make it accessible for only a select list of purposes.
Curious to know how you can build super-secret applications of your own?
Well, that’s the whole purpose of this guide. Let’s dive under the hood!
Huge amounts of data are left unused. This is because enterprises are extremely afraid of data leaks and exploits. But if they could harness the valuable pools of data at their fingertips, they could unlock a new wave of innovations and business models, as well as collaborations between entities that don’t trust each other by default.
We’ve all heard people and enterprises say:
“We’d love to share data with third parties,
… but always under our control,
… if I agree with the objective,
… and if I can authorize the beneficiary on a case-by-case basis.”
At iExec, we’re all-in to advance and democratize confidential computing. Making a developer’s journey as delightful as possible when interacting with our marketplace is at the core of what we do.
We’d like to show you a simple solution to build applications that make use of digital assets while protecting these with the highest level of security. We’ve hidden the complexity of blockchain and hardware enclaves, which are the backbone of our solution, to make it super simple to use.
Preserving data privacy and ownership during all of the data’s life cycle is not an easy process. We protect data in all of its stages: at rest, in transit and while it is being used. On the one hand, protecting data at rest and in transit have well-established solutions with file encryption (e.g. RSA, DES) and secure communication channels with TLS protocol.
On the other hand, Trusted Execution Environments (TEE) is an emerging solution to secure data during its processing and solves the trust issue of data sharing. Blockchain allows to ensure strict data ownership and strict control on its usage. The data never gets revealed to the purchasing parties. Thanks to the technology, governance rules are enforced by smart contracts, and data transactions can be audited by any involved party.
To dive into this tutorial, no advanced development skills are required, the tooling we propose is quite simple.
iExec SDK is a clear and simple tool enhancing all interactions with Ethereum blockchain.
Building an SGX-based application is also a seamless process.
The solution is based on the SCONE framework, provided by Scontain. This framework enables the secure execution of containers and programs using Intel® SGX. Developers will build their applications adding layers on top of existing enclave-ready docker images.
The app we showcase is coded in Python, but other languages are supported, such as Javascript, C, C++, widen the field of possibilities.
The iExec Explorer tracks and displays all transactions going through the iExec platform.
Very basic programming knowledge in Python and common cloud services are required.
The tutorial showcases how to build your application that monetizes an algorithm you want to keep secret.
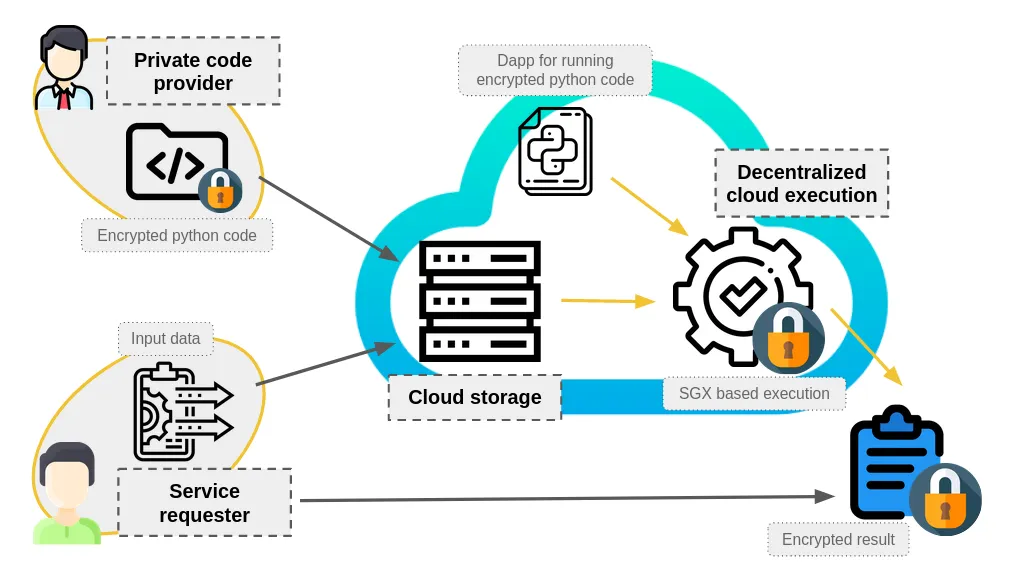
You will discover step by step how to create a confidential computing application and get familiar with the core features of the iExec:
Ok, let’s get into it!
Disclaimer: The tutorial can be completed in around an hour, only if you are extremely and exclusively focused on it. Don’t hesitate to take your time.
Free demo, no crypto or technical requirements needed, Just log in with your Google Account !developers.iex.ec
➡️ https://developers.iex.ec/goal
Video: iExec Completes Whitepaper and Presents New Adoption Roadmap