
The desire to communicate privately is a constant in human history. The Roman Emperor Julius Caesar adopted codes and ciphers to communicate with his generals during the Gallic Wars.
The past is littered with stories where cryptography has played a leading role, whether Mary Queen of Scots plotting to bring down the English Queen Elizabeth or Marie Antoinette corresponding with her secret lover.
Codes have developed and become increasingly complex, to the point where machines, the precursors of modern computers, had to be created to support and break them. Such machines were famously shown in the film The Imitation Game, where the German Enigma machine played a starring role.
Although cryptography was primarily used for military operations, its use quickly expanded to individuals, businesses, and governments, as concerns over secure communication grew significantly. The thought of a world where every message, every file, or every transaction is public and available to anyone rightly fills people with fear. Cryptography, though, exists to ensure this fear does not become a reality.
Today, cryptography drives digital communication whether for governments securing state secrets or citizens sharing selfies. Cryptography underpins secure digital communication and enables trust across the internet, including Web3.
And as the decentralized framework of Web3 grows in attractiveness and importance, the significance of strong cryptographic principles is only amplified.
In a Web3 context, it is common to use ‘crypto’ as a shorthand for cryptocurrency even though the term originally referred to cryptography. Yet cryptography has a broader role than just underpinning cryptocurrencies and blockchain applications.
While it is certainly critical to security and privacy in this context, cryptography is a much wider field, and it supports secure digital communication, data integrity, and user privacy in many domains.
Cryptology vs. Cryptography vs. Cryptanalysis
When discussing a subject like cryptography, it’s useful to begin by defining some key terms and clarifying the differences between them.
First, there is cryptology. This is an umbrella term for the field and represents the science of secrets. Then we have cryptography. This word derives from the Ancient Greek words kryptós meaning ‘secret’ and graphein meaning ‘writing’, and this ‘secret writing’ refers to the art and science of protecting secrets by designing defence protocols..
Where you have codes and secret communications, though, you also have people who want to break those codes and read those messages. The techniques used in such efforts are known as cryptanalysis.
While cryptology technically encompasses both defensive (cryptography) and offensive (cryptanalysis) domains, it is the word cryptography which is most commonly used to describe the field.
Why Privacy & Confidentiality Matter
Two other terms bearing defining are privacy and confidentiality. Though often used interchangeably they actually refer to slightly different concepts.
Privacy refers to an individual and their right to control their own personal information. Whether it is personally identifying information, personal preferences, healthcare data or financial details, a person’s right to privacy is a right valued by all.
Confidentiality, on the other hand, is not a right but a duty. People or organizations with access to personal and private information have a duty to keep it safe and free from unauthorized access, so, to keep it confidential.

Cryptography has these following four core security objectives: :
Several other security objectives such as anonymity or revocation also exist. Depending on the context and specific needs, a system is generally considered secure when it meets one or several of these objectives. For example, a system providing confidentiality and privacy has to meet at least the above four security objectives. When systems are breached and private data is accessed or leaked, it usually means one or more goals were not met.
Within cryptography there are some low-level algorithms known as primitives. These primitives are designed to do one thing in a precisely defined and totally reliable manner, and they are the basic building blocks of any cryptographic system. Three primitives and their applications include:
Keyed and unkeyed primitives are both important in the context of Web3 and combine to improve the security of systems and power increasingly efficient crypto protocols.
Symmetric and asymmetric cryptography depends on cryptographic keys. Just as a physical key is a means to lock or unlock a door, cryptographic keys can be seen as a means to encrypt and then decrypt data, but not only that.
There are two types of cryptographic keys: symmetric (when the same key is used to encrypt and decrypt data) and asymmetric (when mathematically linked keys are used).
Keys consist of a certain number of bits of information. For example, the Advanced Encryption Standard (AES) can use key sizes of 128, 192 or 256 bits. Currently, 128-bit keys for AES are considered sufficient for securing data. However, organizations seeking to guard against future quantum-computing threats can employ 256-bit keys to obtain the same security level.
Yet even with modern threats like key-breaking quantum computers in mind, all public and private key cryptography is built on a principle first espoused in the 19th century. Dutch cryptographer Auguste Kerckhoffs believed that a cryptosystem should remain secure. This should be true even if everything, except the secret key, is known to the public.
Consider the following historical examples of cryptography in action:
This is a simple substitution cipher made famous by its instigator, Julius Caeser. A message is first composed in plain text (for example, “HELLO”) and then encrypted using a substitution algorithm as in the diagram below.
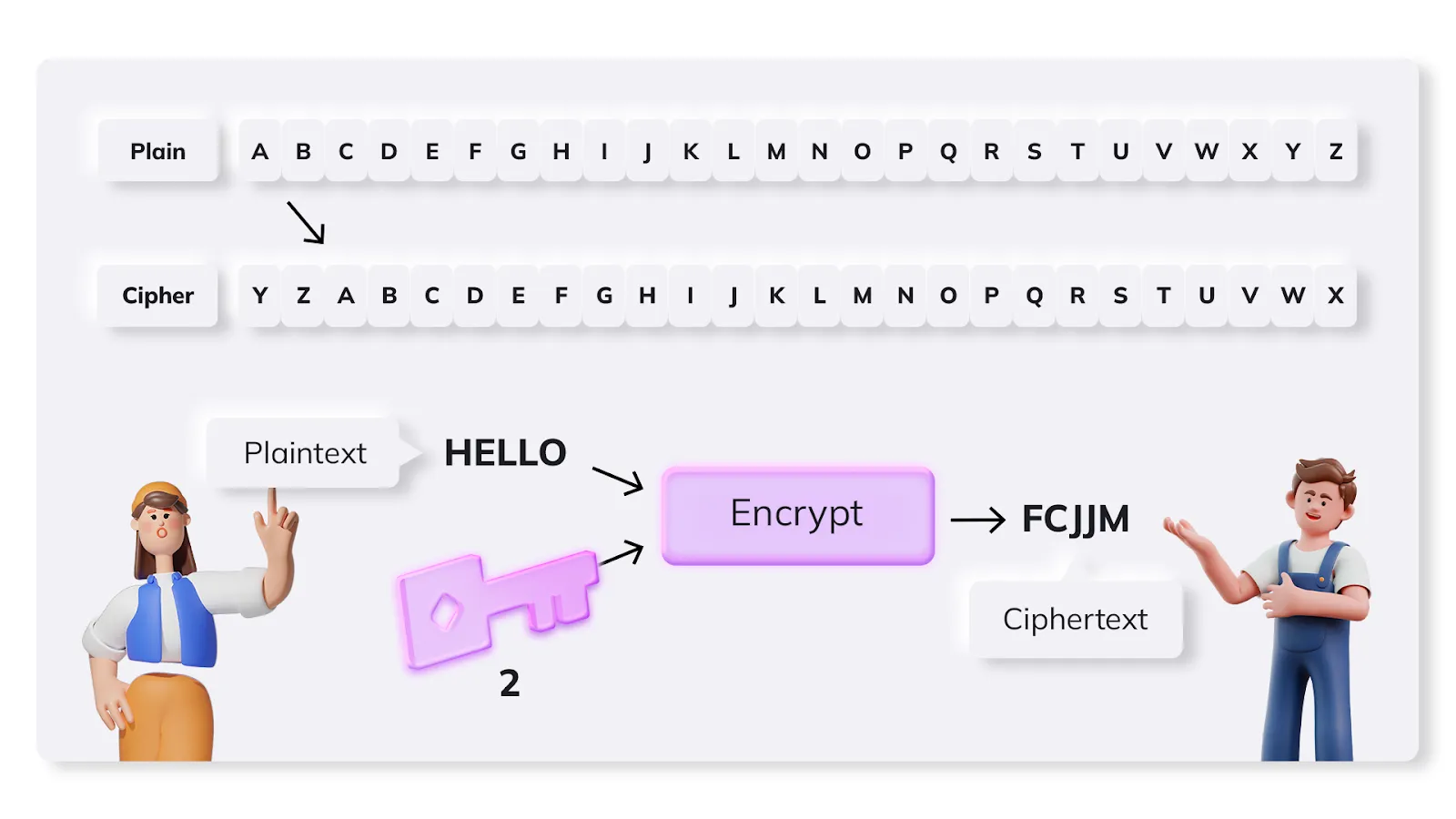
Each letter in the plaintext message corresponds with a letter two places previous in the alphabet. The key to encrypt the message is 2. This key creates substitutions that result in the cipher text “FCJJM.”
To decrypt the message, the cipher text is substituted for its plain text counterpart using the same key as in the diagram below.
As long as the recipient of the message knows the key (2) used to encrypt the message, it is easy to generate the plain text message “HELLO” from the “FCJJM” cipher text received.
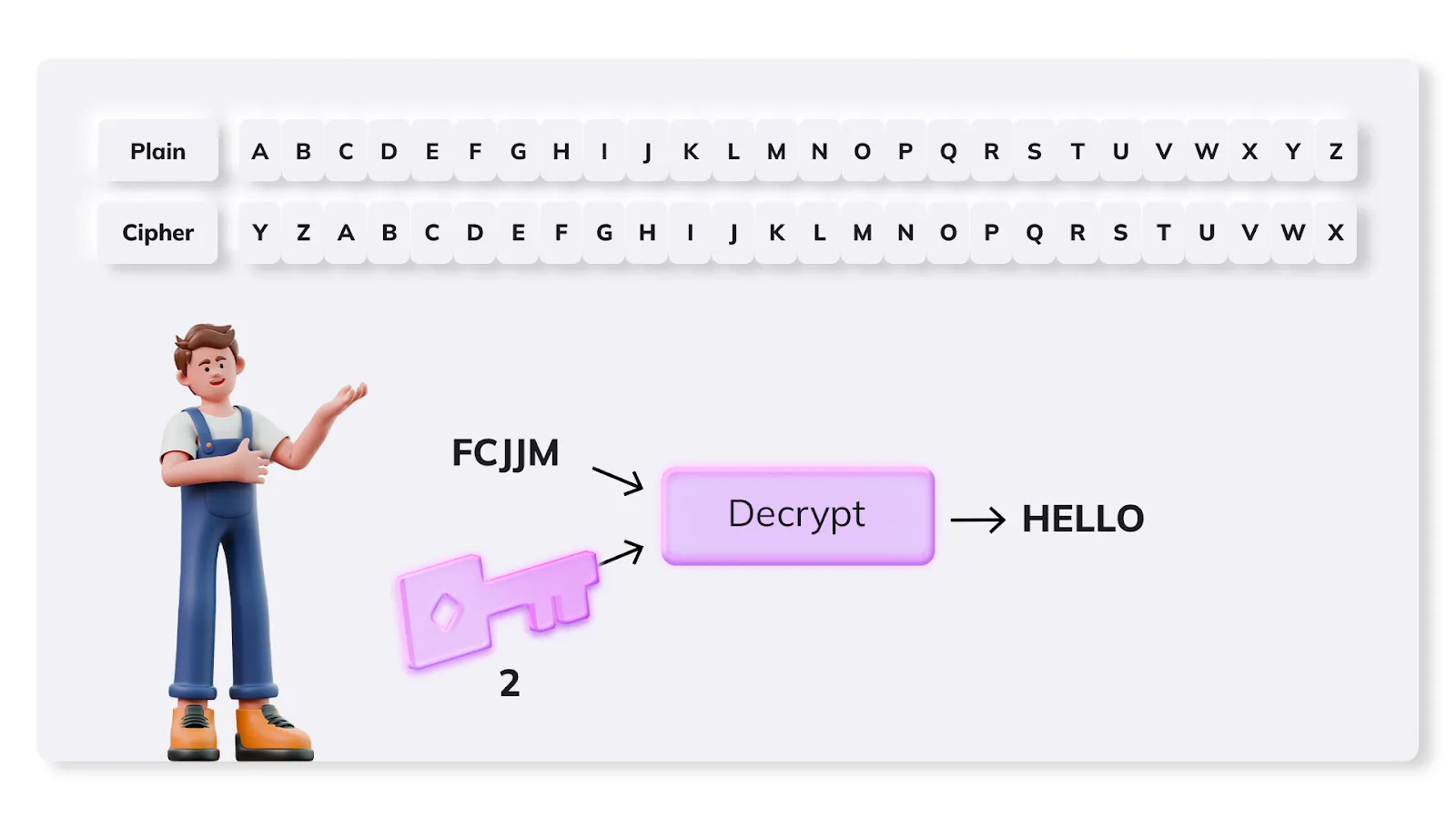
While useful for the Roman Emperor, such basic substitution ciphers are far from secure in the face of modern cryptanalysis. The Caesar Cipher is vulnerable to an efficient brute force attack and would be cracked within seconds using modern computing power.
Symmetric key ciphers do not rely on simple substitutions to transform plain text into cipher text. Instead, someone uses a secret key to encrypt the message, so that, as shown in the diagram below, the word “Hello” becomes “hG7eBxi9.” The same key is then used to decrypt the message by the recipient revealing the original message.
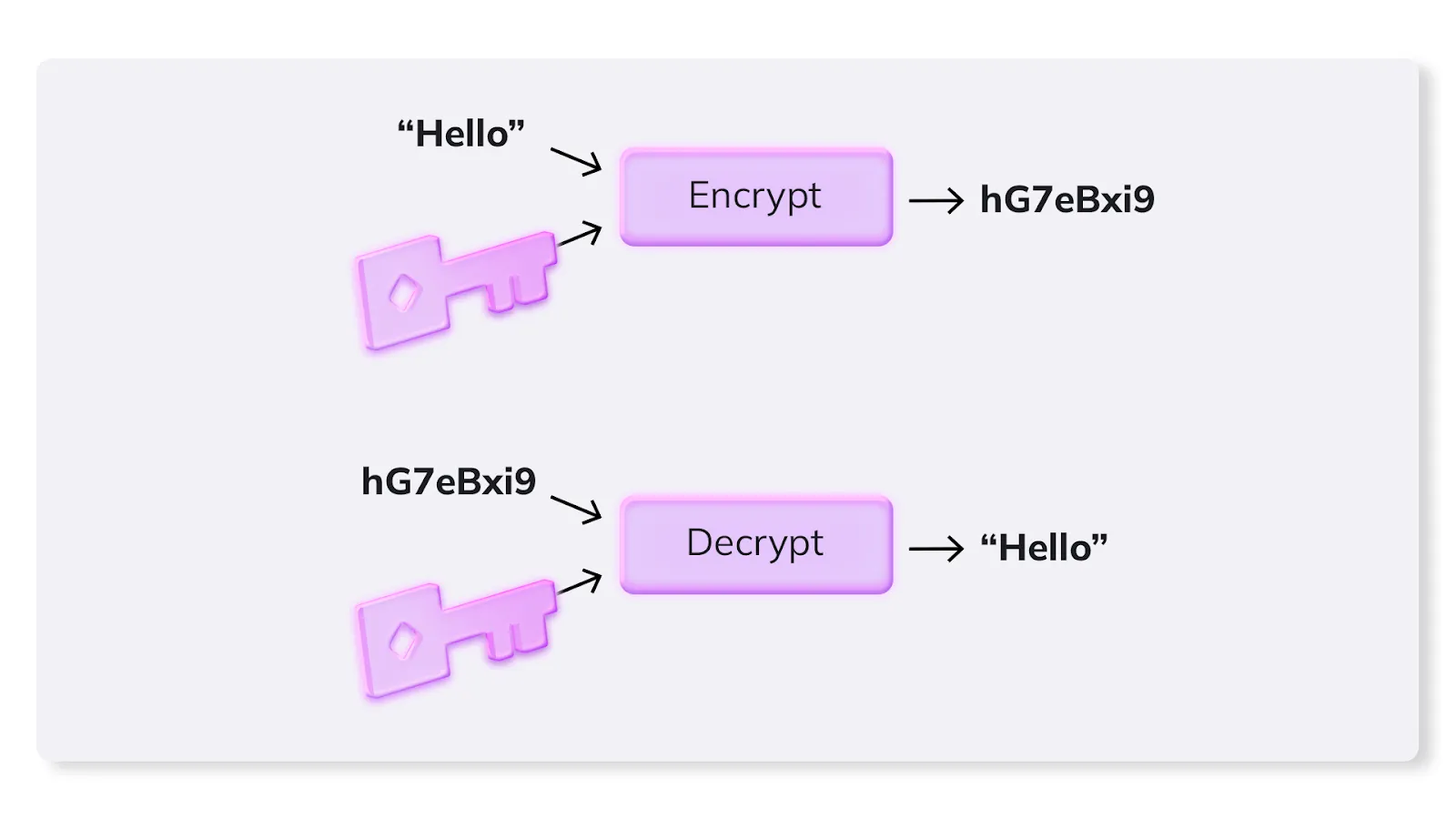
As long as the secret key remains a secret, this cryptographic approach aligns with Kerkhoffs’ principle. However, should the secret key fall into the hands of a bad actor, all messages intercepted could be decrypted easily.
So, what are the chances of a secret key being exposed? As Benjamin Franklin once wrote, three may keep a secret if two of them are dead. In other words, with just a single point of failure, it is possible for someone malicious to decrypt all private messages encrypted with a secret key alone. Little wonder, then, the world of cryptography has embraced asymmetric cryptography.
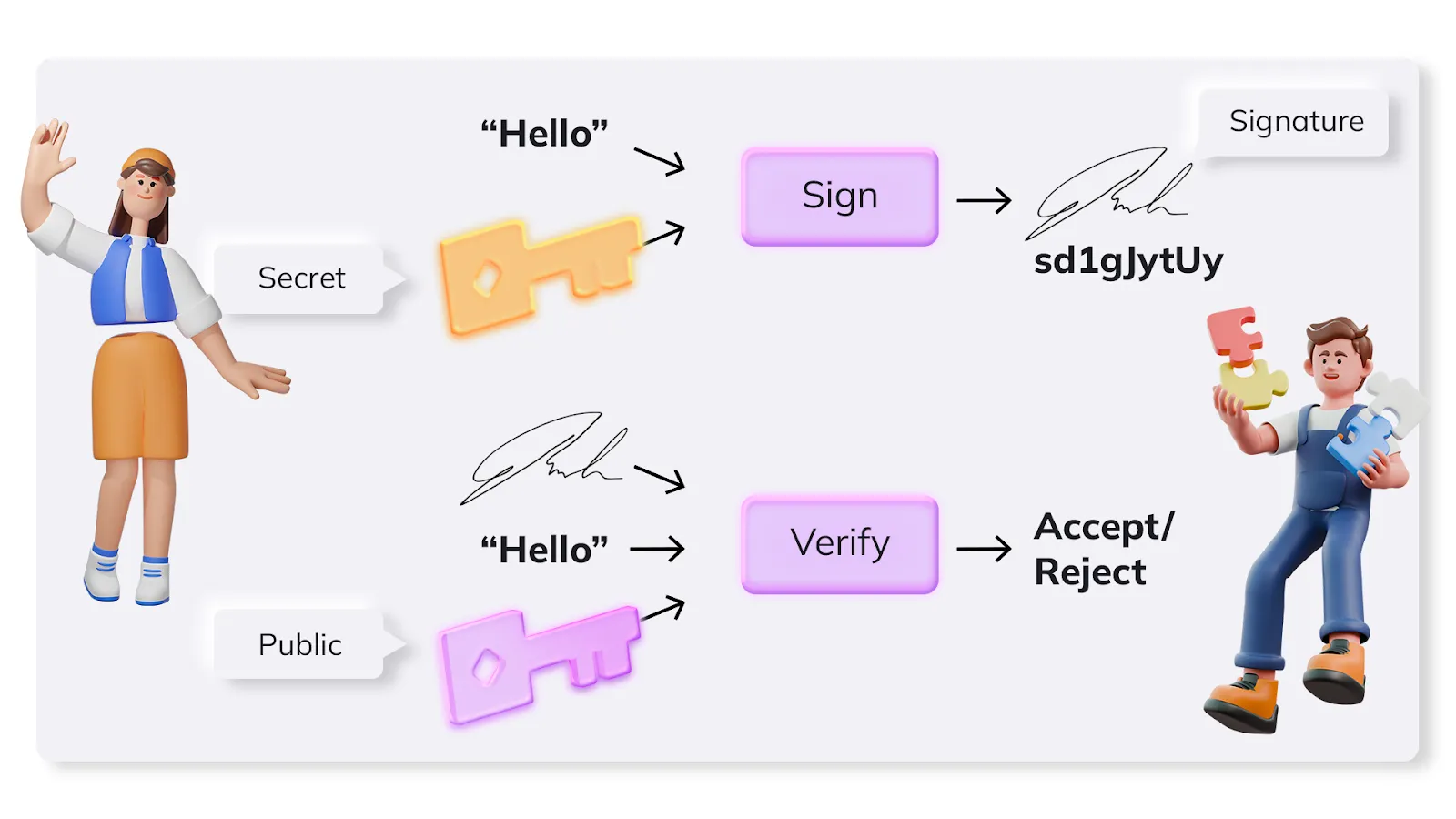
Public-key cryptography sees the message encrypted and decrypted with both a public key and a secret key. The public key, as the name suggests, is available to all but messages received can only be decrypted with the related secret key.
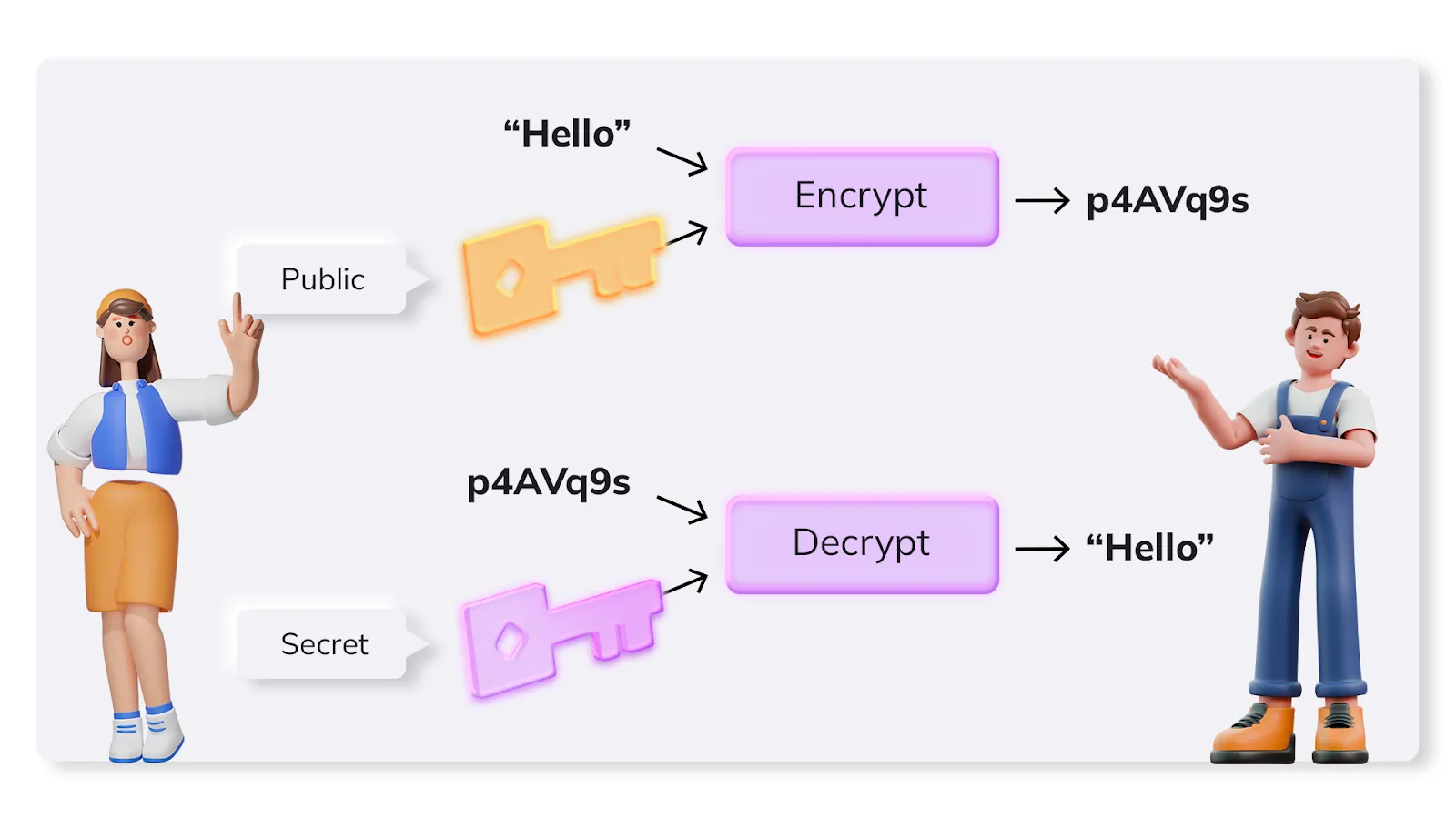
The advantage of asymmetric ciphers is that the secret key does not need to be shared between parties which want to securely communicate. In line with Kerkhoffs’ principle – the secret key remains private to its owner, while only the public key used for encryption is public and so available to anyone wishing to communicate with him. Journalists and others will share their public keys. This helps them have secure, encrypted talks with sources.

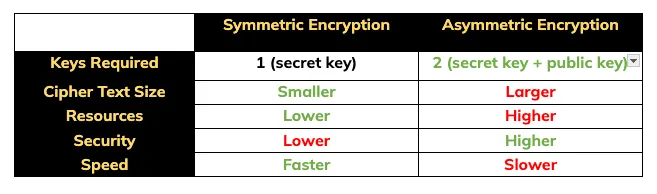
Comparing the symmetric and asymmetric approaches allows us to identify a few core differences.
Symmetric encryption uses one secret key. This method creates smaller cipher text from plain text. It also uses fewer resources to encrypt and decrypt the message. Additionally, it is usually faster to send a message. However, securely exchanging the secret key between parties is a challenging task.

Asymmetric encryption, on the other hand, uses both a secret key and public key to encrypt and decrypt messages. This makes for a relatively larger cipher text that uses more resources to encrypt and decrypt and is generally slower to transmit. The big upside is that it is relatively more secure as the secret key is never shared and the public key reveals no information about the secret key.
Three final areas where we can compare symmetric and asymmetric encryption are known as integrity, authentication, and non-repudiation. This involves assessing and confirming that the sender of the message is who they purport to be, that the content of the message and the data is correct in content and origin, and that the message cannot be denied or un-sent later.
Symmetric encryption of data, even at AES standards, provides only confidentiality. Asymmetric encryption also provides confidentiality but adds integrity (via hashing, described below), authenticity and non-repudiation (via digital signatures).
Both symmetric and asymmetric encryption can be configured to guarantee integrity, authentication, the former via AES and MAC and the latter via, for example, RSA encryption. Only asymmetric encryption, however, enables the use of a digital signature that can guarantee non-repudiation.
Non-key primitives also play a part in cryptography, in particular hash functions. Hash functions help keep data private. They create unique, small, fixed-length versions of data. These versions help to prove that the data stays intact, also called integrity.
For example, a hash function used to create a 6-character hash value turns whatever plain text is entered into a 6 character string no matter whether the plain text is “Hello World” (as in the example below) or an entire works of William Shakespeare.

Hash functions are designed to be one way, unlike key encryption where decrypting the cipher text is part of the design. This one-way property makes hashing a popular approach to securing login data on websites, in recording transactions on the blockchain, and authenticating senders on messaging platforms.
As the web has evolved, so too have cryptographic techniques. In the early days of the web, for example, data was centralized and largely read only. A user would log on to a webpage and read what was found there with limited possibilities to interact.
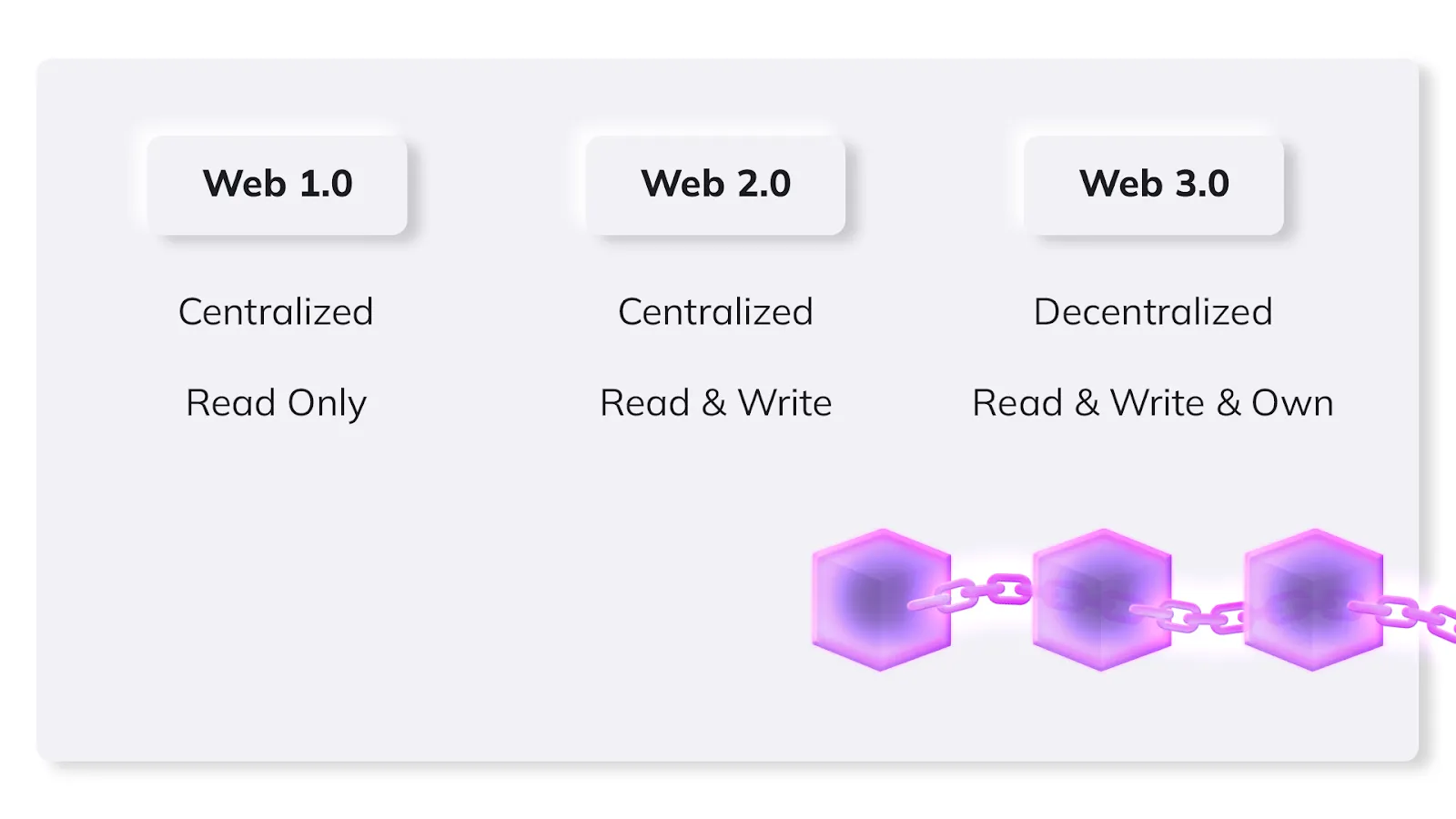
The Web 2.0 world, though, changed this paradigm and an era of user generated content (UGC) reinforced centralized data structures by enabling a true read-and-write web.
Now, with the rise of Web3, the paradigm changes again as data and computing is decentralized and users read, write, and – crucially – own their data. Central to the Web3 world is the blockchain technology, which is secure, functional and trusted due to cryptography protocols.
In Web3 terms, a block is a digital structure to store transaction details, with a transaction being any type of interaction between parties such as a transfer of funds or an activity on a physical or digital asset.

A blockchain is a chain of blocks where each block stores transactions in a distributed manner without any central authority. The ‘chain’ in blockchain refers to the chronological organization of the blocks, with new blocks only ever being added to the end of the chain. One of the fundamental innovations of blockchain lies in its design for immutability; once a block is added and validated, it becomes difficult to alter or delete.
Interacting with a blockchain-based system requires users to have a wallet, a digital collection of keys with which to sign their transactions, as well as an address which is a sequence of characters used as a public identifier.

As a leader and industry innovator in Web3, iExec is well-versed in Web3 cryptography and supports cutting-edge cryptographic protocols.
iExec’s technology couples decentralized computing with a built-in blockchain protocol to power a web where privacy, ownership, and monetization are core to the developer and user experience.
Privacy for users and confidentiality for developers is assured thanks to the decentralized confidential computing (DeCC) iExec champions.
Traditional data security principles protect data when it is at rest and when it is in transit. Confidential computing goes a step further and protects data when it is in use, too, closing the data security loop and ensuring maximized data privacy.
Decentralized confidential computing combines the trust and security of confidential computing with a decentralized blockchain. This creates a computing environment that offers the best of both worlds.
iExec has been a leader in DeCC for a long time. In 2018, it partnered with Intel on the Trusted Compute Specifications for the Ethereum Enterprise Alliance. In 2019, it became the first Web3 company to join the Confidential Computing Consortium.
iExec’s Bellecour blockchain is a proof of contribution blockchain helping scale the company’s confidential computing platform. Like other blockchains, it relies on the fundamental cryptographic primitives such as hashing and digital signatures.
The iExec marketplace leverages symmetric primitives to encrypt datasets and a combination of symmetric and asymmetric primitives to encrypt application results. The iExec Secret Management Service (SMS) handles user secrets. It stores and provides these symmetric secrets to authorized Trusted Execution Environment (TEE) applications on the iExec network.
With its DeCC environment and Bellecour blockchain, iExec uses cryptographic principles to manage sensitive data while providing secure and user-friendly Web3 solutions.
Web3 relies on fundamental cryptographic principles which have a history stretching back to ancient times. The blockchains of Web3 are built on the back of the symmetric and asymmetric cryptography of the Web 2.0 world, with additional privacy enhancements flowing from a decentralized internet broadly and DeCC specifically.
Web3 companies like iExec are bringing secure, confidential computing to the online domain and helping to deliver a safer, more private, more secure digital space for all.
iExec is the trust layer for DePIN and AI.
iExec enables confidential computing and trusted off-chain execution, powered by a decentralized TEE-based CPU and GPU infrastructure.
Developers access developer tools and computing resources to build privacy-preserving applications across AI, DeFi, RWA, big data and more.
The iExec ecosystem allows any participant to control, protect, and monetize their digital assets ranging from computing power, personal data, and code, to AI models - all via the iExec RLC token, driving an asset-based token economy.